Recently at InfoSec18, I attended a demonstration of live, real-time, security threat hunting. I’d go into more detail but, for all intents and purposes, I was left feeling empty. The build-up was highly exciting, but the demo was dull, didn’t showcase the product, nor provide an insight into hunting security threats.
So, to pick up my spirits – and in line with some research we’re conducting – I thought I’d create an article about hunting some security threats on the internet. For this I’ve picked a real-life security threat and the data shown is just as I found it (all be it with some redaction).
BTW, the OSINT in my title is: open-source intelligence.
The security environment
Security threat hunting relies on a few services being in place, mainly having a service which can be polled and secondly having log files (ideally centralized).
| COMPONENT | PURPOSE |
|---|---|
| Firewall | To allow or prevent internet traffic. Also enables logging of traffic. |
| Published Service (Honeypot) | An internet accessible service which will be open for attract network activity e.g. a telnet server, SSH, FTP, SMB or RDP server. |
| Logging | We need a mechanism to record connections and system activity. |
| Centralised Log Service | When hunting across a company network a lot of data is generated. Hunting without a central log source is possible but is time consuming and complicated. |
“Log all the things”
The lab already has a Palo Alto firewall on the perimeter, but for the Windows server we needed a centralized log solution. There’s several commercial and free services available, for this project we decided to use Microsoft Operations Management Suite (OMS). We chose this because it’s low cost, centralized and cloud based, is easy to implement, and provides security analytics and alerting capabilities.
The security honeypot
There are several commercial and open source honeypot tools available. These are generally based on Linux distributions and they enable you to offer up services (telnet server, SSH, FTP, SMB, or RDP server) which will emulate services while keeping you safe.
For our honeypot, we used a Windows Server virtual machine (2016), fully patched with remote desktop enabled. We configured RDS to allow insecure connections to bypass network level authentication so that we could publish on the internet. We then set complex passwords, installed SYSMON (with the swift on security config) and installed the OMS agent (as well as configuring OMS to collect all the relevant logs).
Finally, our honeypot was ready. So, we setup a NAT and security rule on the firewall to expose the service, now all we had to do is wait!
Bees in our honeypot
We started to see activity very quickly using a search of OMS using the following query:
search *
| where Type == "SecurityEvent" and EventID == 4625
| search "Microsoft-Windows-Security-Auditing"
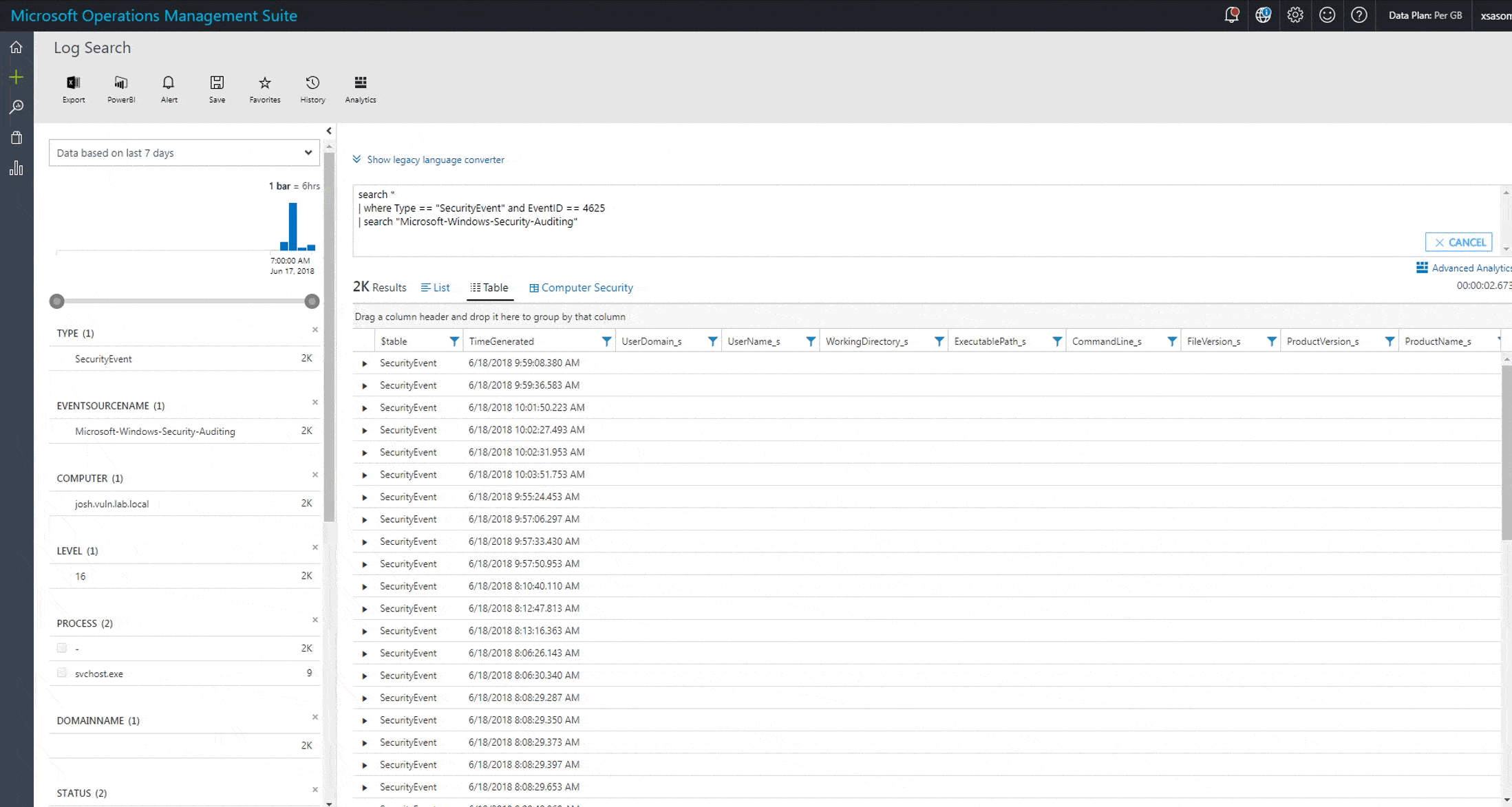
This query shows many failed logins (recorded in the Windows security log):
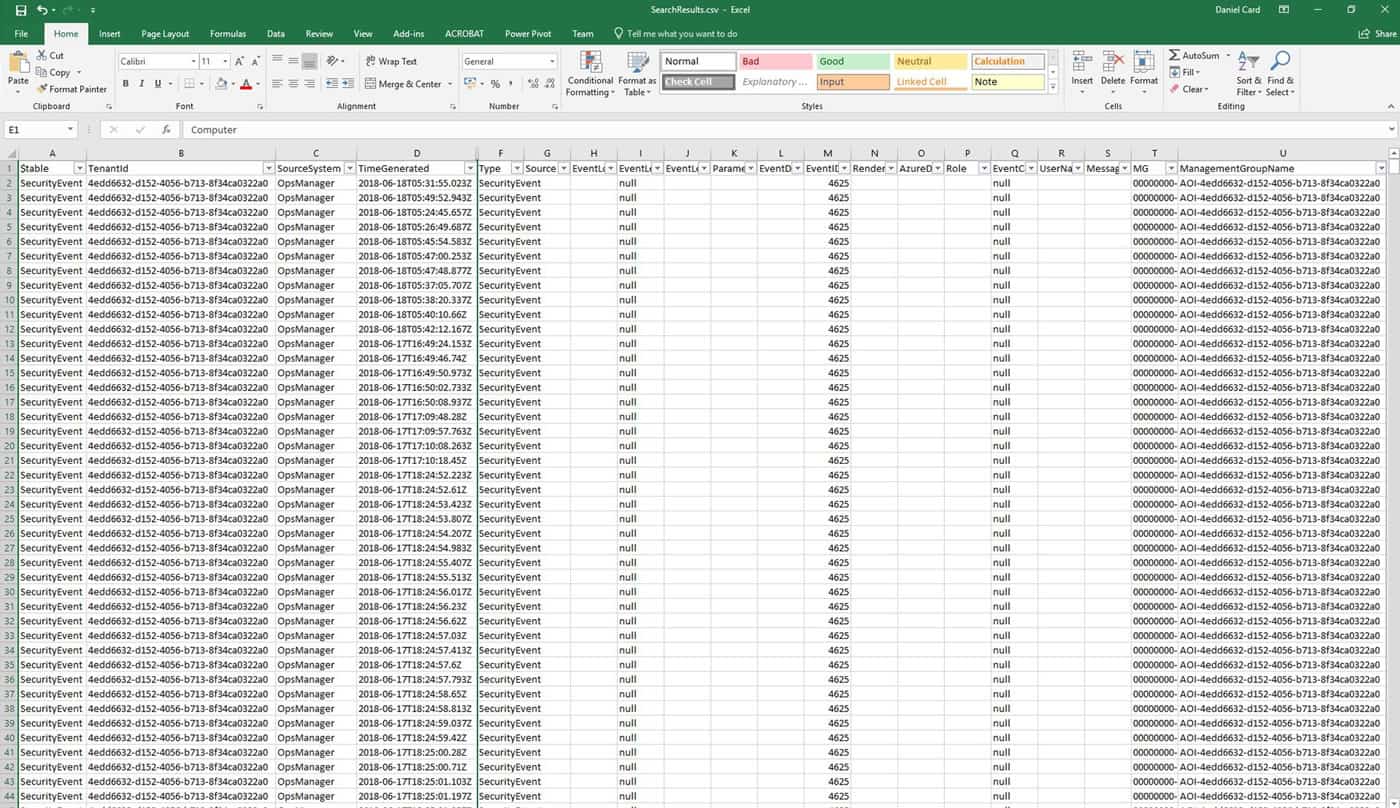
From the OMS console we exported the data into Microsoft Excel:
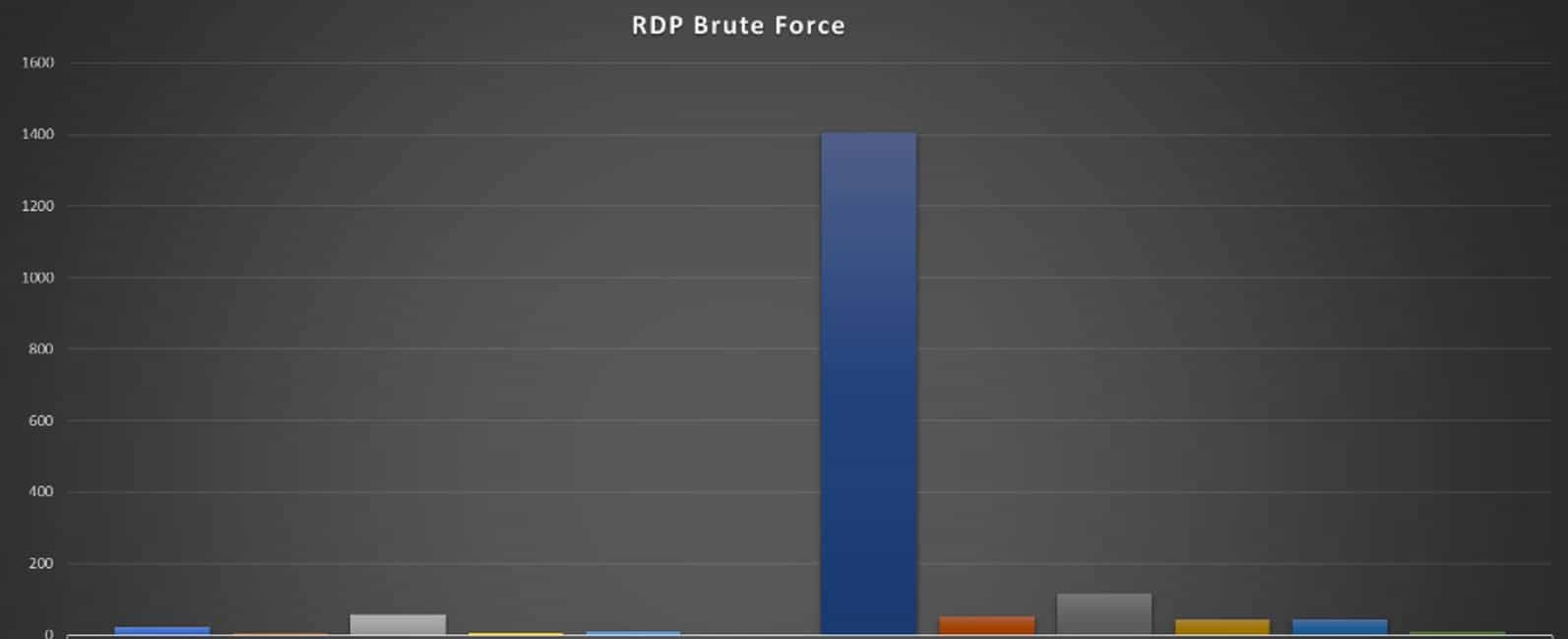
From here we created a pivot, outlining the number of request against each IP.
Immediately we can see an active source IP, time to go on an open-source security intelligence gathering mission. Here we are going to check several sources:
- Shodan
- Alien Vault OTX
- MXToolBox
- Virus Total
- AbuseIPDB
Shodan – shows a UK location
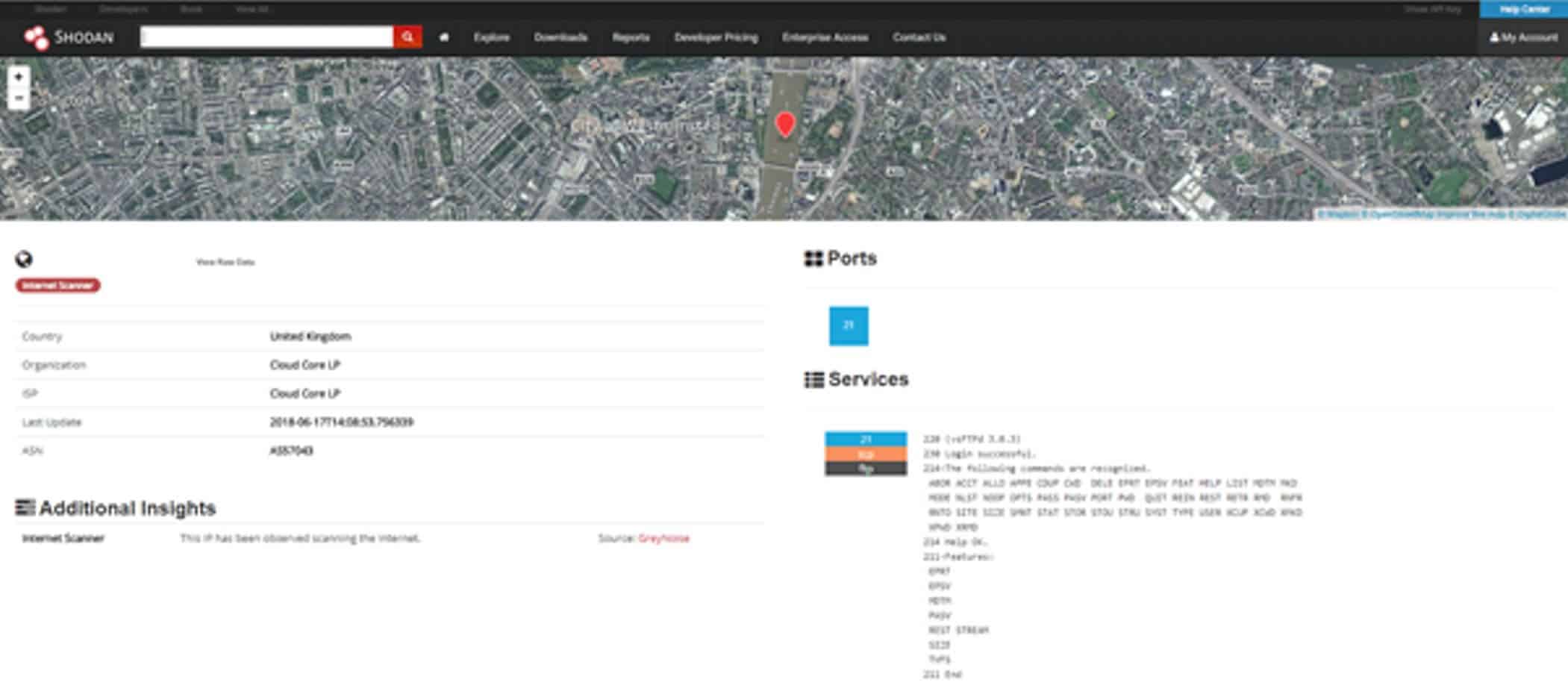
Interestingly, we can see FTP services open-accepting anonymous connections:
Status: Connecting to xxx.xxx.xxx.xxx:21...
Status: Connection established, waiting for welcome message...
Status: Insecure server, it does not support FTP over TLS.
Status: Server does not support non-ASCII characters.
Status: Logged in
Status: Retrieving directory listing...
Status: Directory listing of "/" successful
Status: Retrieving directory listing...
Status: Directory listing of "/" successful
Status: Disconnected from server
A quick NAMP of the service shows only one file is present:
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 0 0 1048576000 Oct 08 2013 1GB.bin
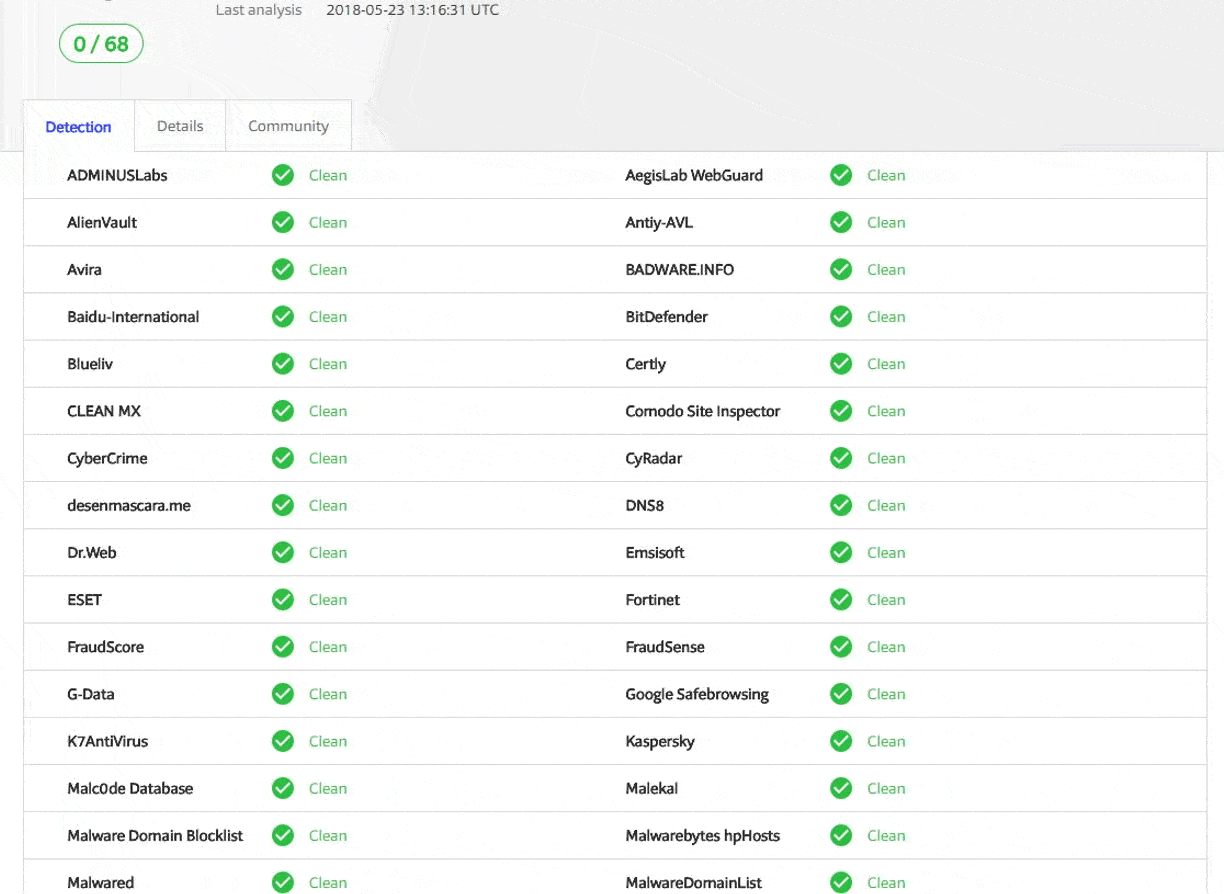
Virus Total
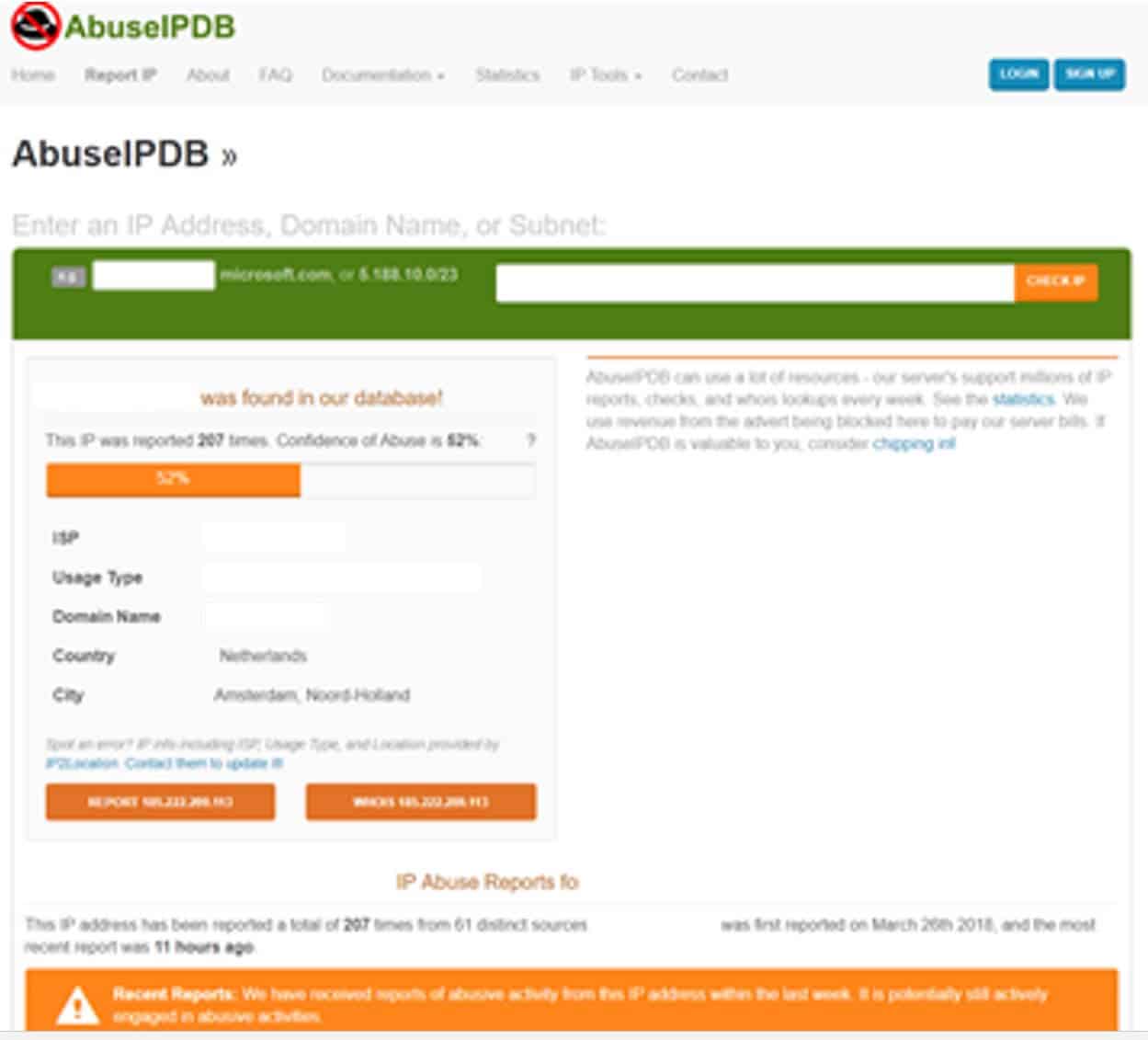
AbuseIPDB – shows a Netherlands location
Attribution is hard
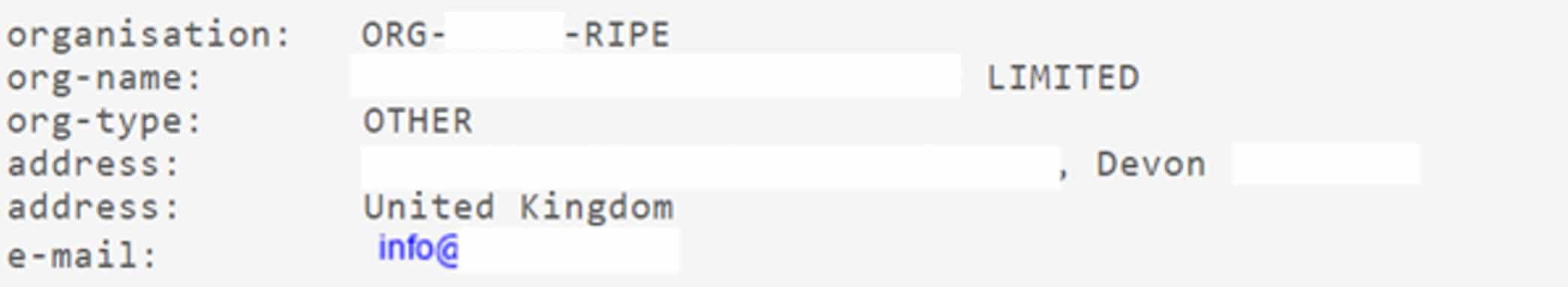
As we can see, there’s conflicting information on the geo-location of this IP (UK or Netherlands) but we can see the IP is registered to a UK organization:
Our next step is to investigate the organization, since it’s a UK company we head over to Companies House, where we can now identify a potential source company and individual, even down to their date of birth and what looks like a home address.
Now we must use some security-analyst input here (as not everything can be backed with science). It’s not a long shot to say that it’s likely this is not a server working for a criminal mastermind (unless it’s a front) but most likely in this scenario the host has been pwn3d by a malicious actor.
We have a contact email, so we’ll notify the organization that we believe their host is compromised.
A layered security defence
We’ve seen a lot of organizations rely purely on perimeter firewalls for security, but as we’ve seen here, even with a next-gen firewall, it’s simply not enough to protect your services from all vectors.
It’s thus essential today to have centralized log management and analysis solution. But remember that even the most advanced solution needs business context, monitoring, and someone available to respond and react (if required) to events.
Have a think about the number of services your organization exposes that allow authentication. Web servers, email services, applications, etc. all present a risk. Now think about that not only from an external perspective but also an internal one.
“Protect all the things!”
So, after investigating the events, we believe that the security threat is legitimate. We’ve reported it to threat-sharing communities, notified the owner, and our internal defense action is to block the IP on our firewall.
It’s important to take both proactive and re-active measures when securing your business, don’t just concentrate on IDS and IPS alerts, you need a joined-up strategy that considers all vectors across the stack.
Daniel Card
Daniel Card began his career within the IT support arena over 17 years ago, and he rapidly worked his way up from frontline services to technical and solution architecture within the first few years of his career, working with a broad range of global companies. This helped him to develop skills in a wide range of both business and technology domains, spanning technical operations, service management, and solution architecture.
Daniel has spent the last 11 years consulting, with a focus on IT strategy, IT business management, enterprise architecture, service management, and cybersecurity.
As the Owner and Principal Consultant at Xservus Advisory Services, Daniel’s mission is to empower businesses to leverage people, process, and technology to reach their ultimate business objectives.

