Hopefully by now you’re aware of the General Data Protection Regulation (GDPR) and the fact that it’s coming into force soon – the 25th May 2018. This means that there’s a new set of processes and responsibilities that your organization will need to be able to handle, some of which include required response times; and these activities have a certain level of governance and auditability around them.
Sound familiar?
What about: incidents with service level agreements (SLAs)? The tracking of changes? Service and support tasks given to teams/individuals in various lines of business?
To me, all these types of processes and activities fall under the umbrella of enterprise service management – because there’s a service requester and provider relationship, where IT service management (ITSM) principles and capabilities can be used to improve performance and service (no matter the line of business).
Understanding GDPR
Under GDPR, “data subjects” (users/customers) will need to be able to log requests for access to their data, log requests to delete data, and make other requests. And there are statutory response times for these requests. This is very similar to logging service requests or incidents and tracking resolution SLAs (using ITSM good practice).
GDPR data subjects also have the right to know what data usage they have consented to. This is rather broad reaching. For example, that an employee has consented to have their PII (Personally Identifiable Information) used to process their salary payments, or the classic customer consents related to marketing information. Both employees and customers have the right to have these consents altered, although there are some restrictions.
Data breaches
The ICO (Information Commissioner’s Office), or equivalent in other EU countries, needs to be informed whenever there’s a data breach relating to PII and potentially there’s a need to inform the data subjects. It’s expected that organizations will have the capability to respond, in a very timely manner, in these situations.
Again, a process – with an SLA – is required to handle this. This is typically triggered from a security incident, which may in turn be triggered from a “normal” incident. A typical process would look like the one shown below:
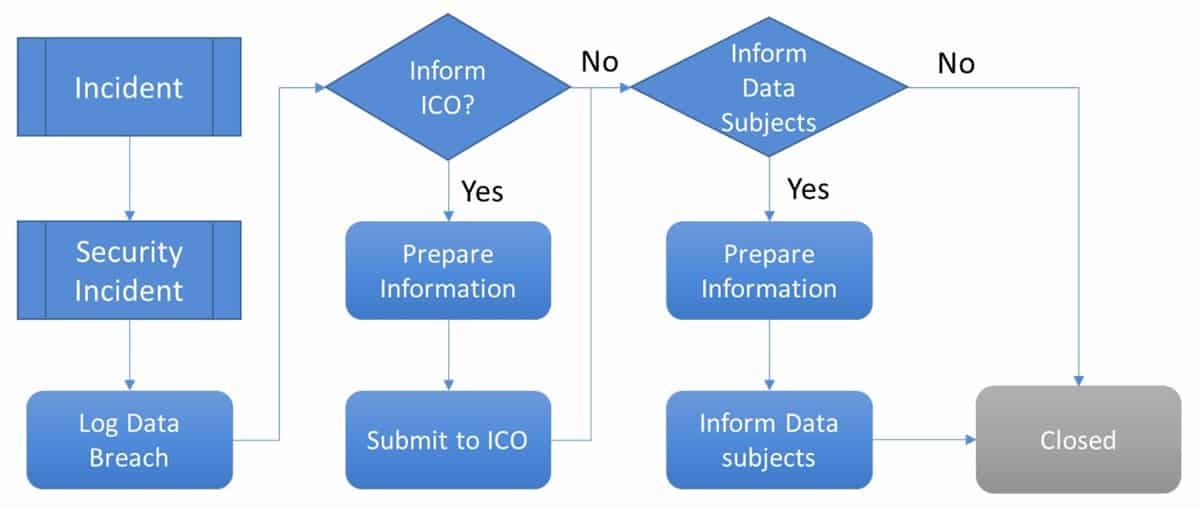
Risk and auditability
The ICO can potentially levy very large fines for non-compliance with GDPR. However, if an organization can show, in an auditable fashion, that it has the right processes in place to handle requests and breach notifications, along with appropriate policies and working practices, then it’s far less likely to attract such large fines.
It has been made clear by recent behavior from the ICO that flagrant disregard for PII and security practices will be punished by larger fines once the powers become available to them. Therefore, being able to show that the required processes are being followed, tracked, and appropriately managed will form an important part of any response to any ICO investigation.
If we think of how changes are logged in an ITSM tool, approvals tracked, or change implementation and back-out plans recorded, we can see how an audit trail is available should anything go wrong. And thus, the answer to the question: “What did you do to control this?” can be answered.
The same applies to GDPR
Should your organization suffer a data breach – due, for example, to malicious hacking – and the ICO investigates, they will want to see that your organization is being a good custodian of data and that GDPR processes and activities are being taken seriously.
Hence, being able to easily show all of these activities, with ownership, dates and times of actions, response times, etc. will certainly help present a positive image and be likely to avoid or reduce potential fines.
Leverage ITSM tools as with other enterprise service management needs
ITSM tools are perfect places for organizations to run their GDPR processes from – providing the required governance and auditability, as well as linking data-breach responses directly to the incident records which initiated them, and thus keeping related data close.
There is, of course, a lot more to managing GDPR requirements than what I’ve quickly covered here.
If you liked this GDPR and enterprise service management article, here are many more enterprise service management articles that might interest you.
Richard Josey
Richard Josey is the Lead Service Management Consultant for Thebes Group. He has over 15 years’ experience in service management, is an ITIL expert, and has helped drive many organizations in their efforts to implement and imbed mature service management processes. This has comprised of numerous Incident, request, problem, change, configuration and release management processes, in a variety of environments.
His approach is always to look for pragmatic solutions, which provide clear benefit and help achieve valuable business goals. Richard is also the chair of the BCS Configuration Management Specialist Group (CMSG), and a committee member of the BCS Service Management Specialist Group (SMSG).
In addition, he speaks publicly, at a number of industry events including BCS, itSMF and Gartner conferences, as well as on a number of webcast and webinars.

